SDP MULTIMEDIA GROUP
Competitor Attacks January 9th 2022
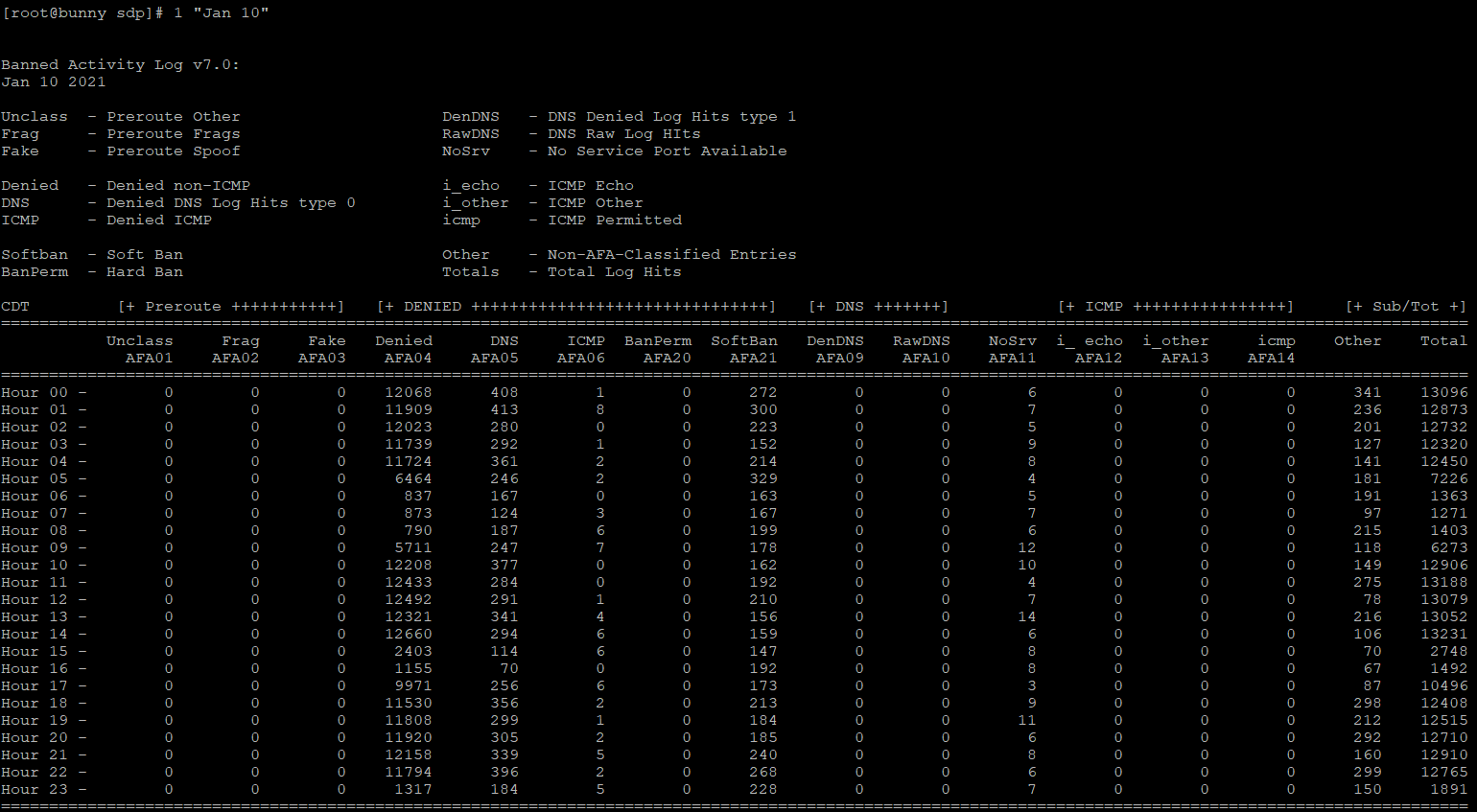
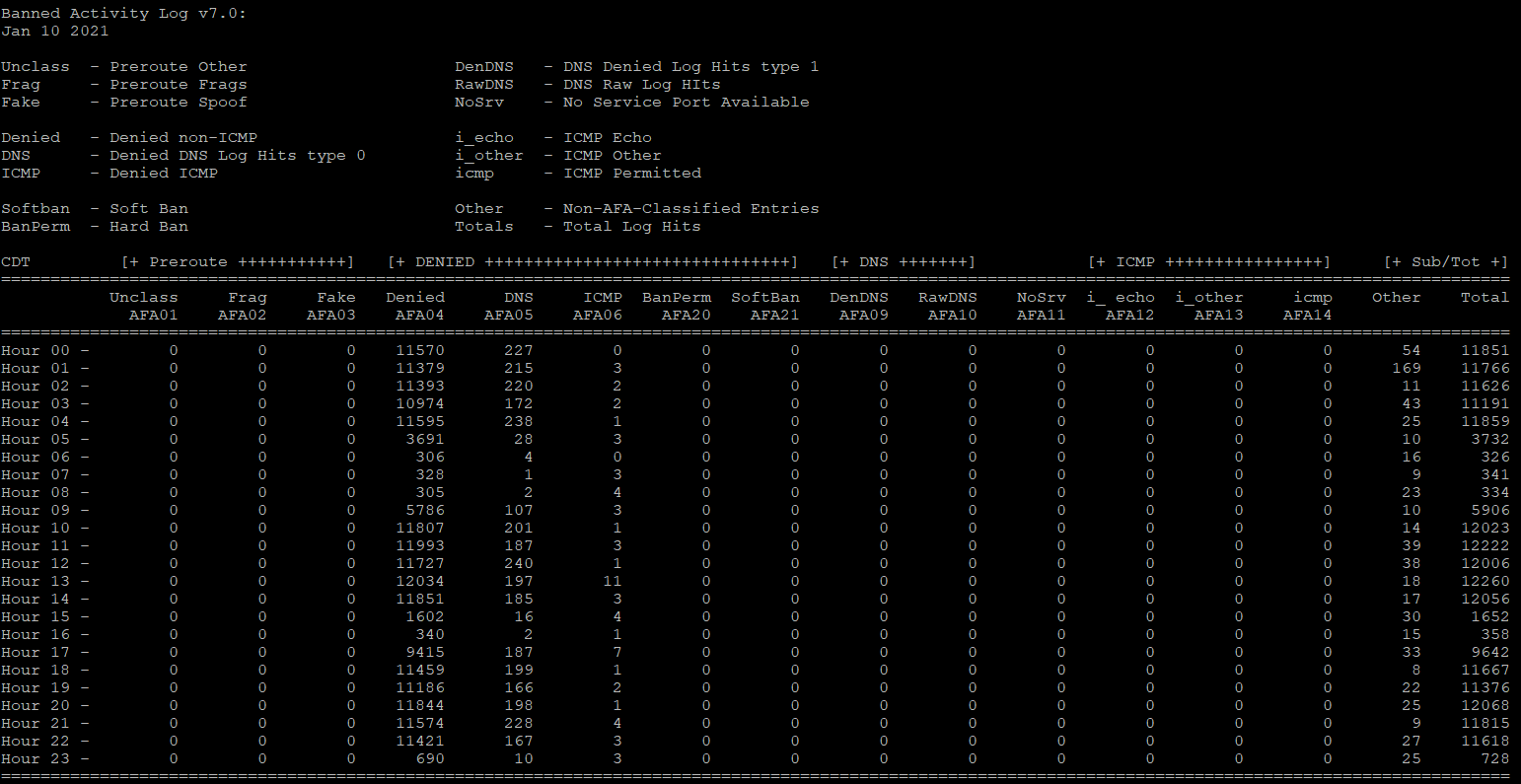
Jan 10 Single Source Dip
Even a moron can see the attacking server dip in the morning on January 10th, showing one criminal actor and in a patttern evident in Central Time Zone identical to Fairway Independent Mortgage hours in State of Texas, attacking our systems. Fairway Independent Mortgage employees have made false claims to suggest we "forfeit" real estate and property to them for $41,000 USD, on welfare of a concealed child taken by threat of murder in 2001 August under criminal fraud for 2001-2022 concealment, to blackmail and extort the Oklahoma family in Pontotoc County throughout 2001-2022 false claims contrary ORDERED POSSESSION to the Oklahoma father refused enforcement by State of Texas and State of Oklahoma.Competitor Attacks Continue
Jan 4 11:11:02 diana kernel: TRACE99: IN=enp3s0 OUT= MAC=e0:3f:49:15:2f:c6:f8:1d:0f:96:f0:12:08:00 SRC=165.227.80.132 DST=firewall LEN=40 TOS=0x00 PREC=0x00 TTL=241 ID=12641 PROTO=TCP SPT=32766 DPT=35135 WINDOW=1024 RES=0x00 SYN URGP=0 Jan 4 11:11:03 diana kernel: TRACE99: IN=enp3s0 OUT= MAC=e0:3f:49:15:2f:c6:f8:1d:0f:96:f0:12:08:00 SRC=165.227.80.132 DST=firewall LEN=40 TOS=0x00 PREC=0x00 TTL=241 ID=22859 PROTO=TCP SPT=32766 DPT=4756 WINDOW=1024 RES=0x00 SYN URGP=0 Jan 4 11:11:03 diana kernel: TRACE99: IN=enp3s0 OUT= MAC=e0:3f:49:15:2f:c6:f8:1d:0f:96:f0:12:08:00 SRC=165.227.80.132 DST=firewall LEN=40 TOS=0x00 PREC=0x00 TTL=241 ID=35640 PROTO=TCP SPT=32766 DPT=40147 WINDOW=1024 RES=0x00 SYN URGP=0 Jan 4 11:11:03 diana kernel: TRACE99: IN=enp3s0 OUT= MAC=e0:3f:49:15:2f:c6:f8:1d:0f:96:f0:12:08:00 SRC=165.227.80.132 DST=firewall LEN=40 TOS=0x00 PREC=0x00 TTL=241 ID=62730 PROTO=TCP SPT=32766 DPT=65099 WINDOW=1024 RES=0x00 SYN URGP=0 Jan 4 11:11:03 diana kernel: TRACE99: IN=enp3s0 OUT= MAC=e0:3f:49:15:2f:c6:f8:1d:0f:96:f0:12:08:00 SRC=165.227.80.132 DST=firewall LEN=40 TOS=0x00 PREC=0x00 TTL=241 ID=40907 PROTO=TCP SPT=32766 DPT=35831 WINDOW=1024 RES=0x00 SYN URGP=0 Jan 4 11:11:04 diana kernel: TRACE99: IN=enp3s0 OUT= MAC=e0:3f:49:15:2f:c6:f8:1d:0f:96:f0:12:08:00 SRC=165.227.80.132 DST=firewall LEN=40 TOS=0x00 PREC=0x00 TTL=241 ID=35668 PROTO=TCP SPT=32766 DPT=23747 WINDOW=1024 RES=0x00 SYN URGP=0 Jan 4 11:11:04 diana kernel: TRACE99: IN=enp3s0 OUT= MAC=e0:3f:49:15:2f:c6:f8:1d:0f:96:f0:12:08:00 SRC=165.227.80.132 DST=firewall LEN=40 TOS=0x00 PREC=0x00 TTL=241 ID=40041 PROTO=TCP SPT=32766 DPT=7362 WINDOW=1024 RES=0x00 SYN URGP=0 Jan 4 11:11:04 diana kernel: TRACE99: IN=enp3s0 OUT= MAC=e0:3f:49:15:2f:c6:f8:1d:0f:96:f0:12:08:00 SRC=165.227.80.132 DST=firewall LEN=40 TOS=0x00 PREC=0x00 TTL=241 ID=17098 PROTO=TCP SPT=32766 DPT=7499 WINDOW=1024 RES=0x00 SYN URGP=0 Jan 4 11:11:04 diana kernel: TRACE99: IN=enp3s0 OUT= MAC=e0:3f:49:15:2f:c6:f8:1d:0f:96:f0:12:08:00 SRC=165.227.80.132 DST=firewall LEN=40 TOS=0x00 PREC=0x00 TTL=241 ID=39305 PROTO=TCP SPT=32766 DPT=46518 WINDOW=1024 RES=0x00 SYN URGP=0 Jan 4 11:11:04 diana kernel: TRACE99: IN=enp3s0 OUT= MAC=e0:3f:49:15:2f:c6:f8:1d:0f:96:f0:12:08:00 SRC=165.227.80.132 DST=firewall LEN=40 TOS=0x00 PREC=0x00 TTL=241 ID=58129 PROTO=TCP SPT=32766 DPT=35939 WINDOW=1024 RES=0x00 SYN URGP=0
As the information shows, attacks from a single offender using cloud ochestration to automate virtual services against our network continues in concert with Demands from Veronica Marie Petersen, a Texas former Nortel Networks website contractor unemployed in 2000 August to 2001, who seeks $41,000 USD in violation of Federal Law on the Oklahoma XXIII-1A Constitutional Right to Work violation and for "forfeiture" of securities, stock, trademarks, copyright, franchise, real estate title, and other "property" specified as protected under the Oklahoma Computer Crimes Act (21 O.S. §21-1952).
Threats published November 14th 2021 have been filed with the Pontotoc County District Court, showing a 2002-2004 and 2007-2012 and 2013-2021 "legal sham" (21 O.S. §21-1533) complaint in concert with 2002 and 2011 and 2021 extortion activity to cause default for civil asset forfeiture sought in a civil contract, violating Federal Law and 586 U.S. ____ (2019) case no 17-1091 rule barring any claims from standing to pay a "500 USD" final judgment rendered in July 2002 by TEXAS FAMILY CODE, and discharged due execution of contract clause also in 2003, and arrived at from a case where Veronica M. Petersen was found "wholly in default" December 2001 by Judge Dee Miller; prior fraud to carry that case forward over the obligation to return a child themed missing and exploited in collateral ransom for kidnapping prohibited by the Hobbs Act.
Company identities used in forgery to carry this attack include "Digital Ocean LLC", "Hetzner.de", and are made in concert with attacks from Ann Arbor (Michigan), Tencent Holdings Co Ltd networks, and known hosts of the "Lostserver" unregistered labor organization acting in this fraud and by name in 2002-2022 extortion to concael a child themed on counter-claim 21 O.S. §21-748.2 "Human Trafficking" for "forced labor" and "debt bondage" so also subject unlimited damages in the third degree by jury trial sought in 23 O.S. §23-9.1 not eligible other limitations or privileges per Oklahoma State Supreme Court ruling on UNCONSTITUTIONAL NATURE of all such terms and Statutes made in 23 O.S. cause; so void TEXAS FAMILY CODE §157.008(d) and other false claims to limit liability in this matter, a fraud and effort to overturn commission in false claims of "not a real business" uttered repeatedly to conceal kidnapping of a child of a business owner to blackmail and extort sustained in 20 year concealment and fraud falsely alleging to the child and public that such member of the Allen/Overton family was "willingly abandoned" on forced taking from a motor vehicle en route to State of Oklahoma from State of Texas on Interstate 75 in INTERSTATE COMMERCE.
Such transfer a contract prior paid and secured by over $10,000 USD in funds to Accounts Payable of VERONICA PETERSEN at Trinity Medical Center, The Colony, TX; and by agreement to seek therapy for domestic physical violence against James Allen resulting in sevre physical injury and attempted murder in 2001 preceding kidnapping of the child at 74 days of age and suspension of all due process by State of Texas to suppress the conduct of their Citizen over the Okalhoma parent and his home state rights and claim for return of the child, a demand refused without legal cause by DALLAS COUNTY DISTRUCT JUDGE DEE MILLER contrary 76 O.S. §76-8 rule, and Inhernent rights of Article II Constitution which prohibit 4th and 14th Amendment violations by a civil court in taking of children to compel labor and peonage, surrender of property, surrender of credit, or other claim to goods not a "sum certain" defined in UNIFORM INTERSTATE FAMILY SUPPORT ACT (Rev 2008), obligated any legal order for registration or enforcement as "child support", and no such order ever registered in State of Oklahoma for enforcement. Acts of enforcement or demands without registration or to coerce a pending civil trial filed Nov 2018, are criminal acts and prohibit enjoyment of such order or beneficts on intimidation of parties outside the civil process using illegal means, barred a lawful debt in collection per 15 U.S.C. §1692d.
Criminal activity in overt acts appears ongoing as of November 14 2021, December 23 2021, and January 1st-4th 2022, in a pattern of psychotic behavior increasing Pontotoc County office physical security after five (5) hit-and-run attacks on U.S. Mail service receptical boxes at the 130 N COUNTRY CLUB RD property in 2015-2021, the last in July 2021.
Use of Security Scanner products or attempts to gain privileges or utlize the network for non-company purposes will be regarded as component to any impact on service or logs and unauthorized use. All traffic is logged for analysis and retained for law enforcement at this time. Video surveillance on premise is obligatory, due to criminal written plan to extort and 11/7 and 11/14 threats coinciding with increased intrusion and prior May 20 2020 physical break-in by two or more persons using heavy duty work trucks to attempt robbery and overcome Office Staff.
All necessary physical security precautions will be taken. Conduct your actions and correspondence as if dealing with a United States Federal Facility and Communications Network Site not open to the general public. Any attempt to trespass may be subject public report and notice. All communications are the property exclusively of the firm, and given over to the firm for public display and circulation in assistance to ending these coercive activities of our major competitors in Texas, Michigan, California, New York, and Florida; and any other jurisdiction from which they launch attacks or execute fraud or other criminal acts or public offenses against this firm.
What we are seeing is an intense effort (127 requests/min) over nine (9) hours this Monday January 4th 2022 by 11:53 am, to suggest a concerted effort to disrupt business in concert with a push to compel State and Federal law enforcement to quash a motion to set aside for fraudulent conveyance per rule 18(b) the claims by Veronica M. Petersen falsely made in State of Texas.
Copyright © 2022 SHADOWDANCERS LLC - ALL RIGHTS RESERVED.