SDP MULTIMEDIA GROUP
Regular Registration Terms: SEVEN ALPHA (PKI) Network
| Main Page | Home | Practical Use |
Seven Alpha is a private academic network, protected by 2048 bit strong encryption (SSLv3/TLS1.2) with client-certificate authentication and VPN private-network access. It provides a workspace for American Dialectic research and development projects, free from Hegelian Dialectic interference.
American Dialectic: Rule of law based on rights inherent in individual persons, and Article II-6 statutory relief obligated.
Hegelian Dialectic: Rule of law based on populist and emotional appeal paired with fraud, force, and threat of murder.
Understanding the Seven Key System
Simple Explanation of What Seven Alpha Is and Does
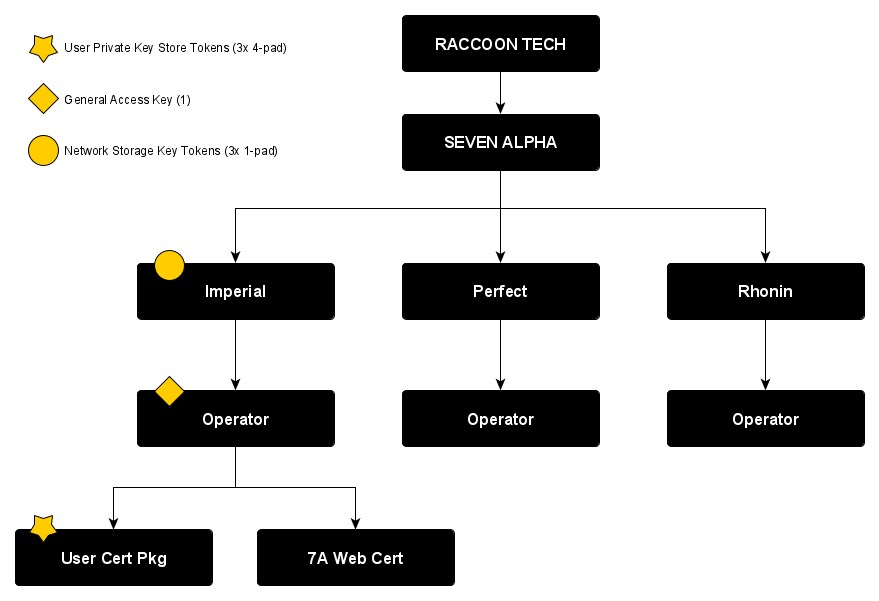
Seven Alpha™ is a secure domain, edge network, and session management system similar to traditional Virtual Private Network concepts. It incorporates a file storage and safety deposit box system for digital block storage devices, allowing users to place and retrieve file systems via SSL transport containing complex encryption device objects - file blocks encrypted separately in multi-cipher multi-layer encryption using three (3) keys and one (1) written password. This ensures data is stored in a format that carriers cannot open, functions like a diplomatic pouch for cold storage and edge user identity protection.
Concepts in this mode require a strong understanding of one-time pad combined with modern cryptography and pre-shared session management for secrets transmission. https://en.wikipedia.org/wiki/One-time_pad
Block Storage and Virtual Servers utilize similar concepts, while Seven Alpha focuses on authentication, shared archival and recovery of block data in additional (3xlayer) encryption, and generic data obljects with additional 3xlayer client encryption signed in using a 4th layer strong crypto-identification for access control. In this manner, data is secure form access by the service prior transmission to the host, removes content otherwise themed a violation of 'perfect security' in one-time encryption of well known TCP/IP patterns thwarding SSL over traditional single-cipher solutions, and allows counter-signature to deny compromised NSK (Network Storage Token / Password) access with a strong use case GAK (General Access Key) which may be tokenized physically like a smart-card chip.
Seven Alpha™ may be used solely for transport protection and authentication, or deep encryption layering up to 6 levels, ideal for contesting quantum grade and state-sponsored decryption technology.
Storage therefore requires the user to validate themselves before the 'vault' decrypts it portion of the 'lock' representing the safety-deposit-box key and vault; while the user must still (optionally) open the lock-box inside the container with their own keys. The validation mechanism allows users to also access services which are only available to members, and rely on a secure key not shared with the public at large, limiting SSL transport exposure by non-participation in general public certificate distribution channels like Alphabet Inc., Apple Inc. and Mozilla browser partners.Access to data in each "protectorate" (Imperial, Perfect, Rhonin, etc) is uniquely signed, and does not carry over to other 'compartments' of the Seven Alpha, allowing users registration to grant privileges solely in their namespace (Protectorate), as well as share in benefits of the community of Seven Alpha.
"Operator" Desks serve as the issuing authority of all end-user keys, like an intermediate certificate for a conventional SSL chain, and ensure that user keys are 2 steps away from the Protectorate Key as well as 3 steps from the Seven Alpha root.
Network Storage Key Tokens (NSK) and User Private Key Store Tokens (UPKS) are the anchor points of the encryption solution, affording the user a set of keys for encryption which require a password, and a counter key set used for the same operation not shared with the end-user or accessible as a function without identification through the fabric or biometric verification as a backup method. Like a national member registry, Seven Alpha thereby affords a strong PAD system to information control paired with real world verification of persons during a failure of traditional cryptographic solutions. Security is a secondary aspect of service provision reliant on strong identity systems affording a 1:1 ratio of user to account not common in other two-factor accounts and registries. User poly-identity is handled in the fabric of the Seven Alpha network, not by creation of multiple accounts to access a service, like most games and businesses today. This affords a stongly-registered user environment with strict behavioral control to enforce a civil code of conduct and limit abuse which impairs most consumer entertainment.
Automation makes the access and use of keys as simple as plugging in a USB and selecting the application, with a one-time password prompt. In this way, it is like a smart-token, but requires user input and a managed / revokable token to prevent loss and track malicious use of compromised tokens. Similar systems are milspec and have practical uses for sensitive systems.
Inherent storage of the user credentials for transport lock inside of a triple-cipher password protected vault prevents copying of keys and brute force attacks from having substantial success, in combination with user login strategies to track fraudulent activity and alert users to key use outside their normal patterns - as seen in other major networks two-factor fraud prevention systems.
Seven Alpha™ is the result of increasing abuse of 'REGISTRY' data by governments to entail and then suspend rights and communication themed anti-govenrment or counter-policy to popular religious movements in pseudo-science, similar to the actions of Marx and Hitler, which promote 'right think' and make civil honors dependent on compliance and subordination to avoid 'wrong think', dissent themed as mental health defects in a pattern of "G.W.F. Hegel" style claims and propaganda. The developer holds a degree in clinical psychology, is a former United States Army Specialist, and publisher in digital media for 25 years. Seven Alpha is designed to meet goals for a strongly registered civil society rule set, and facilitate certain kinds of information-warfare games which require these technologies to operate a persistent world themed 'science fiction' similar to Dystopian Fiction. The side effect is a strong registred data storage and management system for distributed strong service fabric across multiple nodes and a scalable security network based on token security.
Seven Alpha™ includes arbitration and resolution methods which differ from the United States and other courts, are specific to United States codes and regulations themed a form of law separate from the United States and its member States, and is reliant upon contract to bind over members to this form of resolution in agreement similar to the Uniform Code of Commerce (UCC) and "Articles of Rome".
Dignity is the primary value sought and cited, in addition to the injury to the dignity of any one a superior value to benefits or other marginalized values in collective bargaining theory of United States civil and criminal courts. In essence, this means a crime against one is a crime against all, and the injury done to any person themed an injury to the individual person of all who may be so required to sit in judgment of the offender. The right to marginalize injury to a person in the intent of creating an implied or general benefit is rejected by Seven Alpha™ and the benefit of the many never themed a value to the injury of any one person a defense.
Formats, language, and customs regarding this process emphasize the patience to hear a defense as well as the role of the individual dignity and ideal of individual rights the purpose of the system of justice, professional standards, and conduct afforded use of the network. This means sexual content themed free speech on other Internet Platforms is not permitted on Seven Alpha™ and all derived exploitation of persons to diminish personal relationships and protection likewise themed a violation of its regulations. This is the point from which the "American Jurisprudence" separates itself from "United States Jurisprudence", reliant on the 586 U.S. case 17-1091 and 588 U.S. case 17-647 ruling in 2019 by the Supreme Court of the United States, whereat SCOTUS sided with the principles of the United States and rejected the claims of the many States in 45 CFR ruling disclaiming human trafficking under color of law, themed gneocide by the Federal Union, and a fraud to embezzle from the Treasury of the United States in separation of children based on secular taking themed "progressive socialism" or "Hegelian" socialism in AJP studies.
American Juris Prudence (AJP) applies Oklahoma Constitutional Concepts to Existing Constitutional Law as a combined privileges and immunities model proposed by Justice Ginsburg (586 U.S. case 17-1091) in her eloquent opinion for the unanimous Supreme Court in 2019 February. Dispute by States in this ruling who seek to retain their "Sovereign Immunity" claims disbarred in 588 U.S. case 17-647 ruling of 2019, further contest the position, from which AJP arrives a strongly typed professional self-regulating body to ensure its members a consistent Constitutional over Statutory Code business enviornment, themed the common law of the American People.
Businesses that want their own sub-organization in this model are screened and granted conditional terms to establish a "protectorate" for their product or service with an "Intermediary" key similar to the "Imperial" and "Perfect" protectorate groups. This affords a fixed rule and arbitration model, appeal, and localized rules to manage and admit or remove members for other enterprise and industrial purposes.
Protectorate groups are entitled to charge whatever they wish for End User Registration in their domain, as is necessary to ensure one natural born person per user account issued is maintained and terms of the Seven Alpha professional regulations and conduct codes are met. In this way, Seven Alpha™ is scalale and affords specialization in multinational communities and without traditional borders or state registration to operate among members, similar to Masonic and other professional fraternities in prior commercial eras. Where a handshake or an endorsement and registration once afforded members in these organizations protection, Seven Alpha™ adapts the concepts to a larger computer-based assembly with fewer elements of a religion nature than traditional organizations of the industrial and colonial era.
Fees are designed to ensure members are capable of maintaining their obligations, registries, and operate according to regulatory conditions similar to the Federal Communications Commission (FCC) of the United States over radio broadcast and digital broadcast media, which has broken down with private cable and packet-switched public Internet technology since 1991. Not-For-Profit and other Special Purpose Registries will be considered grants for use where fees may not be appropriate and use case is clearly made in the interest of Dignity and of the King of Kings, a model supporting the inherent dignity in all natural born persons to be free from bondage, slavery, genocide, corruption of blood and other forms of civil death in a digital society.
Practical Uses
- AM24 Game Design
- Secure Forums
- Professional Conference Security Telepresence
- SideChannel Coordination
 Seven Alpha (7A) Registration verifies a United States resident for access key issue.
User verification and background check to limit one account per natural born person,
who must be 24 years of age per verifiable documentation. Protectorate Services
include private key issuance for customers to access a restricted area only for the
member and their keyholders, and the ability to issue keys at-will to those non-members.
Seven Alpha (7A) Registration verifies a United States resident for access key issue.
User verification and background check to limit one account per natural born person,
who must be 24 years of age per verifiable documentation. Protectorate Services
include private key issuance for customers to access a restricted area only for the
member and their keyholders, and the ability to issue keys at-will to those non-members.
Intermediate CA Parties are known as 'Protectorate' Administrators on Seven Alpha. Each 'Protectorate'
has the ability to issue keys for their respective zones to an unlimited number and scope, governing
their own administrative domain. This solution removes the cost of numerous SSL certs for very large
site networks, and allows better granular control over SSL security to specific hosts as intended in
the openssl implementation.
$4000.00 Annual Registration - Intermediary CA Registration w Approval - Terms and Conditions Apply - U.S. Residents Only
Seven Alpha: End User Registration
 End User Registration - includes a certificate for access to general Seven Alpha services not granted by
a Protectorate-only area, such as account extended services and cross-protectorate service access features
of the Seven Alpha Network. While a Protectorate Key will grant end-user access to their domain, any features
that may be transferrable to other domains or products outside that network require an End User Registration.
Does not include protectorate key services or hosting network account. Identity verification for AM24 is a
requirement of End User Registration, and assure customers that End User accounts are operated solely by the
person named in the application and by no other authority or user per agreement. End User Registration
ensures standing in Seven Alpha for all official matters, arbitration, and remedy afforded. Protectorate
Consumer Certificates do not afford these rights, and grant only benefits cited in each authority rules related.
$60.00 Annual Registration - End User Registration - Terms and Conditions Apply - U.S. Residents Only
End User Registration - includes a certificate for access to general Seven Alpha services not granted by
a Protectorate-only area, such as account extended services and cross-protectorate service access features
of the Seven Alpha Network. While a Protectorate Key will grant end-user access to their domain, any features
that may be transferrable to other domains or products outside that network require an End User Registration.
Does not include protectorate key services or hosting network account. Identity verification for AM24 is a
requirement of End User Registration, and assure customers that End User accounts are operated solely by the
person named in the application and by no other authority or user per agreement. End User Registration
ensures standing in Seven Alpha for all official matters, arbitration, and remedy afforded. Protectorate
Consumer Certificates do not afford these rights, and grant only benefits cited in each authority rules related.
$60.00 Annual Registration - End User Registration - Terms and Conditions Apply - U.S. Residents Only
Copyright © 2019 SHADOWDANCERS LLC - ALL RIGHTS RESERVED.